Checkpoint Endpoint Client Download For Windows
Click here to download checkpoint VPN on MAC. Open the file Checkpoint-MAC.dmg. Double click Checkpoint-MAC.dmg. At the introduction, press continue. Vera crypt for mac. At the licence accept, press continue, then agree. At the installation type, press install. At the summary section, once the installation was successful, press close. Download endpoint security vpn for free. Security tools downloads - Check Point Endpoint Security by Checkpoint Software Inc. And many more programs are available for instant and free download. Read reviews, compare customer ratings, see screenshots, and learn more about Check Point Capsule Connect. Download Check Point Capsule Connect and enjoy it on your iPhone, iPad, and iPod touch. Securely Access all your corporate resources from your iPhone and iPad through a Virtual Private Network (VPN) tunnel.
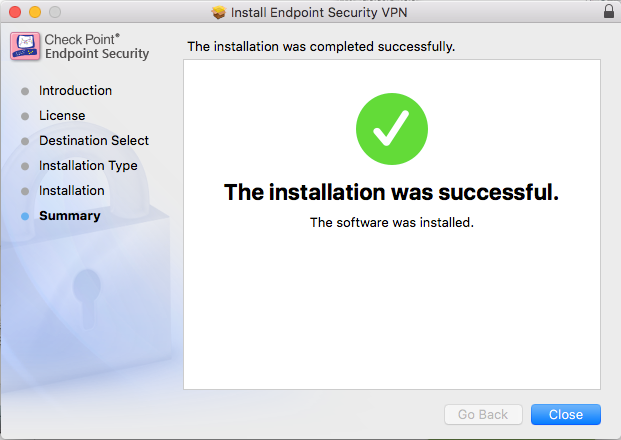
Checkpoint Endpoint Client Download For Windows
Click here to download checkpoint VPN on MAC. Open the file Checkpoint-MAC.dmg. Double click Checkpoint-MAC.dmg. At the introduction, press continue. Vera crypt for mac. At the licence accept, press continue, then agree. At the installation type, press install. At the summary section, once the installation was successful, press close. Download endpoint security vpn for free. Security tools downloads - Check Point Endpoint Security by Checkpoint Software Inc. And many more programs are available for instant and free download. Read reviews, compare customer ratings, see screenshots, and learn more about Check Point Capsule Connect. Download Check Point Capsule Connect and enjoy it on your iPhone, iPad, and iPod touch. Securely Access all your corporate resources from your iPhone and iPad through a Virtual Private Network (VPN) tunnel.
Checkpoint Endpoint Security Download Mac 10.15
|
